Auto-run + auto-download = automatic viruses
Autostart Worm Breaks Mac Malware Silence! That headline is from 1998. If it sounds familiar, it is because sometimes the more things change, the more they stay the same. The Autostart-9805 worm spread because Quicktime 2.0 had functionality to automatically run software as soon as a CD, floppy, or network volume was accessed. Meant as an ease-of-use feature, this auto-run functionality was easily exploited for trojans and worms.
Apple learned: in Quicktime 2.5, they added an option to disable autostart. In Mac OS X, there is no way to even turn autostart on.
Auto-run functionality is dangerous. This is not news. Just last summer the news broke that Sony was automatically installing rootkits on Windows computers whenever a music listener put a Sony CD into their computer’s CD drive. Sony’s rootkit was easily exploited by other hackers to gain full access to an infected system. That’s what a rootkit is for. Sony took a lot of heat for this—and deservedly so.
Because Apple did not enable CD auto-run on Mac OS X, Mac OS X was (and is) immune to this kind of rootkit.
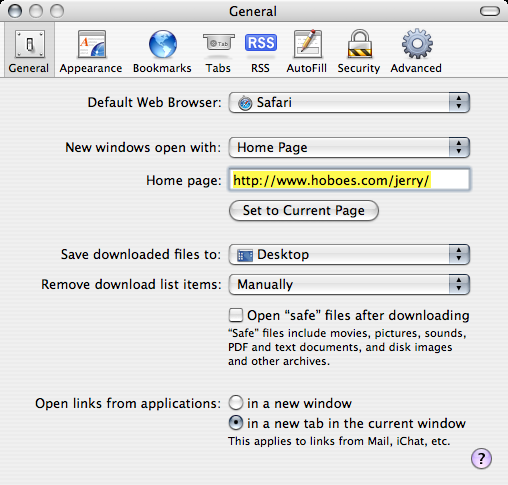
Now we find that there is an auto-run vulnerability in Safari, but this is not new for Safari either. Two years ago, Apple had to react to a Safari vulnerability that could cause untrusted scripts to run in Apple’s “Help” program. This vulnerability also hinged on the Open safe files after download functionality in Safari. Apple responded, not by disabling auto-run, but by further restricting what it considers safe files.
That kind of response always leaves open the likelihood that they’ve forgotten something. What they’ve forgotten is that, for security purposes, the distinction between documents and applications is practically nil. In this case, the “document” opens in Terminal, which then runs it as a script. But Terminal isn’t the only software whose documents are scripts. Microsoft Office documents can include scripts—the term macro virus is almost synonymous with Office malware. Graphics software such as GIMP and Photoshop have their own scripting languages which can access files on your computer.
As applications move more and more towards being dynamic, auto-run becomes more and more dangerous. “Dynamic” means, “able to change things”. When combined with auto-run functionality, that means malware. Web browsers are supposed to be safe sandboxes, but when documents get opened outside of the web browser, that sandbox disappears.
Auto-download
The other problem—and the one that makes Apple’s intransigence potentially dangerous for web browsing—is that too many sites rely on redirects to perform downloads. Instead of clicking on a file and downloading the file, sites such as VersionTracker.com and SourceForge.com will have you click on a link, go to a web page, and have that web page redirect to a download. Web browsers should block automatic downloads. Nothing should get downloaded unless the user clicks on that item. Unfortunately, too many sites use redirects to perform downloads.
When a web browser encounters a redirect that redirects to a downloadable file, it continues to display the current web page, but it also downloads the file. Some browsers even do so in the background, invisibly to the user. That’s wrong. Automatic download is a way of placing files on your computer that you don’t know are there until you run across them later. Even if the download doesn’t automatically open, it remains there as a future danger. What are the chances that you would know not to double-click “map.jpg” on your desktop? What are the chances that your friends will know that you did not download that innocuously-titled file?
Download-on-redirect means that any web site you go to can transfer files to your computer without your requesting those files. This means that when there is a vulnerability such as Safari’s open safe files after download, that vulnerability can be exploited without any user interaction. But it also means that any web page can send you a payload that you—or some less aware person using your computer—might click on later.
If a redirect results in a download, browsers should block that download. At the very least, browsers should warn the user that this download is the result of a trick easily exploited by viruses and give them a chance to cancel.
Administrative accounts
Too often, operating system writers such as Microsoft and Apple pretend that their defenses will always hold. They expend little or no effort towards minimizing the damage that will be done when their Maginot line is bypassed or breached.
The greatest blunder is that they expect that most users will do all of their work from an administrative account. This means that when malware does get through, it now has access to an administrative account with far greater privileges.
One of the things that auto-run software will do, for example, is try to take over your computer. That’s what a rootkit is for. Getting access to your account is one thing, and allows the malware to play havoc with your personal files. But it doesn’t let them grab or change the personal files of other users on your computer, and it doesn’t offer as many possibilities for using your computer to spread to or attack other computers.
Under normal circumstances, there shouldn’t be any way to gain root access from any account, but all software has bugs, including operating system software. Sometimes these bugs will result in vulnerabilities that allow “escalation of privileges”. These vulnerabilities are usually easier to take advantage of if the malware is able to access an “administrative” account. So it is much safer to do your normal work from a non-administrative account.
But both Windows and Mac OS X set up only an administrative account for you when you set up your computer. Because of this, most users do their normal, everyday work from an administrative account.
Basic security recommendations
These three issues—auto-run, auto-download, and administrative accounts—greatly exacerbate the risk of acquiring malware, and the damage that the malware can do once acquired. You can greatly reduce these risks if you:
- Ignore any unknown files that appear in your normal download folder;
- Do not use an administrative account for general use;
- Do not allow any software to automatically download unknown files;
- And do not allow any software to automatically open documents or applications.
This advice applies to Windows as well as Mac OS X. You can turn off auto-run on CD insertion, and you should. The examples here will be from Mac OS X, because that’s what I’m using.
Turn off automatic downloads
Make sure that your browser will at least notify you whenever a download starts. You can then cancel the download or trash the resulting file. For example, on the browsers available to me:
- Camino 1.0 does not appear to have any way of turning auto-download off. Make sure that you don’t have “Close downloads window” or “Open downloaded files” checked in Camino’s Downloads preference pane.
- Firefox 1.0.6 will let you switch to “Ask me where to save every file”. It will then pop up a save dialog for every file before it downloads the file. By default, however, it might ask you the first time for a particular type of file, but will auto-download after that.
- Mozilla 1.7.8 and Netscape 7.2 will always pop up a “save as” dialog when downloading files. As far as I can tell, you can’t even turn it off (which is good).
- Opera 8.5.2 will pop up a “save as” dialog by default. You can only turn auto-download on in the “Advanced” download preferences. Once you do this, though, the only way to turn it off is to go through each MIME type one by one to verify that “Do not ask for folder” is unchecked for that MIME type.
- Safari 2.0.3 does not appear to have any way of turning auto-download off. The first time a download occurs, the “Downloads” window will pop up; if you put it behind a window, it will stay there for any subsequent downloads. Make sure that you don’t let it go behind anything: either keep it visible, or always close it when you’re done.
Turn off auto-open in Safari
Safari’s Open “safe” files after downloading should say “Open files I guess are safe, but might not be.” Because that’s all this option does is guess whether or not a file is safe to open. It has a list of what is safe, and that list can—and has been—wrong. In this case, Safari can be tricked into sending a script off to the Terminal application. In the past, it could be tricked into sending scripts off to the Help application. What it means is that any software that can run scripts—Word and Terminal, for example—becomes an easy target for Safari-downloaded files.
Turn it off. It’s easy and all it means is that when you download a file you’ll also have to double-click it in the Finder to open it. Safari’s “downloads” window will show you exactly where it is in the Finder.
Turn off auto-run in Windows
I don’t use Windows enough to track down how to do this. It is apparently easy in some versions of Windows and not so easy in others.
Moon Valley Software has what appears to be a comprehensive list of how to disable auto-run in Windows.
Create a non-administrative account
On Mac OS X, you can easily do all of your work from a non-administrative account. But you first have to set one up. This would have been a lot easier if Apple had set it up for you automatically when you turned your computer on for the first time. But it still isn’t difficult. The only difficulty is getting all of your files from your admin account to your new account.
- In System Preferences, go to the Accounts preference pane. On Mac OS X 10.4, you’ll hit the “+” button in the lower left to add a new account.
- If you just purchased your computer, add a new account and do not check “Allow user to administer this computer”. You’re done.
- On the other hand, if you have been using your computer for a while, and you’ve got a lot of stuff in your current administrative account, make this new account an administrator also, by checking “Allow user to administer this computer”. Make sure you remember its password.
- Once you have an administrative account set up, choose the account you’ve been using, and uncheck “Allow user to administer this computer”. Continue using this now non-administrative account for your general computer use.
When you need to perform an administrative action, such as copying an application into your Applications directory, you can do so from your non-administrative account. Mac OS X will ask you to type an administrative username and password to authorize the administrative change.
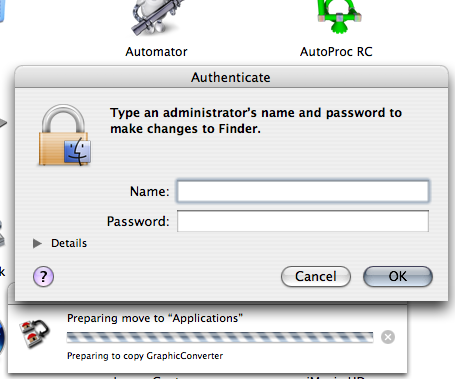
If you approve of the change being made, type in your administrative username and password.
You should only click “Authenticate” if you know why it is asking you this. Never authenticate random requests on your computer!
After clicking the Authenticate button, you’ll be asked for an administrative account name and password.

Again, be careful when your computer asks you for an administrative account name and password. Make sure you know why it needs this information.
Safety starts with you
Unix-like operating systems such as Mac OS X have a well-deserved reputation for security. But that security will fail if you ask it to. None of the changes discussed here can protect you if you choose to download viruses and if you choose to open unknown files. Be aware of what you’re downloading and be aware of what you’re opening. If something seems odd (you don’t remember that file being there, for example), take a moment to think about it.
Always know why you are being asked for your password, and never type your password unless you know why you need to.
Despite all of the hype it’s been receiving, this latest Safari vulnerability remains unexploited. There are no known viruses taking advantage of it. The other recent malware news for Mac OS X is Leap-A. It’s a trojan: it requires that someone on your computer accept an unknown file, double-click that unknown file to decompress it, and then double-click the uncompressed file that results from the decompression.
Please don’t do that. A little common sense goes a long way.
- Autostart Worm Breaks Mac Malware Silence
- “Nearly three years after the last Macintosh-specific virus appeared on the scene, a new piece of Macintosh malware has appeared. The worm, which is designed to overwrite data files, has spread rapidly in the desktop publishing community in Hong Kong, where it was first spotted.”
- Rootkit at Wikipedia
- “A rootkit is a set of software tools frequently used by a third party (usually an intruder) after gaining access to a computer system. These tools are intended to conceal running processes, files or system data, which helps an intruder maintain access to a system without the user's knowledge.”
- 2005 Sony CD copy protection controversy at Wikipedia
- “The XCP software can be prevented from installing in several ways. First, a user can refuse to purchase such copy-protected CDs. Second, disable autorun so that the software will not run automatically. Perhaps the safest alternative is to use an operating system which the software does not automatically install itself on, such as Linux or Mac OS X.“
- Enable/Disable Autorun
- Several different ways of turning auto-run off in various versions of Windows.
- Infoworld Agrees: OS X “Threats” Overblown
- “The ‘critical’ label affixed to the viruses by security vendors are alarmist, inciting a code-red threat level for potential security risks that Mac users can avoid through commonsense precautions.”
