The last four digits of your social security number
Because of identity theft and privacy concerns, many businesses ask for only the last four digits of our Social Security numbers. There seems to be an assumption that only four digits of a nine-digit-number shouldn’t be a concern.
“How hard would it be for someone to guess the first five digits of my Social Security Number if they only had the last four?”
The obvious answer is, about 9,999 times easier than if they didn’t know the last four.
In fact it’s even easier than that. Your Social Security number is not a random set of digits. The last four numbers are created sequentially. They have no other relation to you. The rest of your Social Security number, however, is determined by where you requested it; usually, this is where you were born.
The first three digits of your Social Security number are an “area number”. If someone can determine what area the person applied for the SSN in, they can determine the first three digits; it is currently based on zip code. There are currently no more than 772 area codes.
You can check the state ranges against your SSN at the Social Security Number Allocations page on the Social Security Administration web site.
The middle two digits are the “group number”. This is probably more difficult to determine, but they are distributed in a pattern. In any case there are only 99 of them, usually less. For any specific area code, the Social Security Administration publishes the highest group number used.
There are also some other Social Security numbers that have been invalidated. For example, if the last four digits are 1120, identity thieves know at least one area code/group number combination that it is not.
When you give out the last four digits of your Social Security number, you are giving out what is probably the least-easily determined part of it. Once a criminal has the last four, if they truly want your identity (as opposed to just anybody’s identity), they ought to be able to bring down the total possibilities to no more than several hundred.
Giving out the last four digits of your Social Security number makes your entire number a lot more vulnerable. Armed with a computer and an on-line authorization site that doesn’t care if an SSN is checked every day, they probably won’t have any problem finding the rest. Your only hope is that they won’t want to.
- July 27, 2016: Are insecurity questions designed to help hackers?
-
If you read this blog regularly, you know that the main purpose of insecurity questions is to help hackers get into your account. This is a testable theory. For example, one of the drawbacks, as far as hackers are concerned, is that the number of answers is unlimited. While it’s likely to be pretty easy to guess what your favorite dog breed is just by watching your Facebook feed, it’s possible that you use an odd spelling, or don’t know what your dog’s breed actually is.
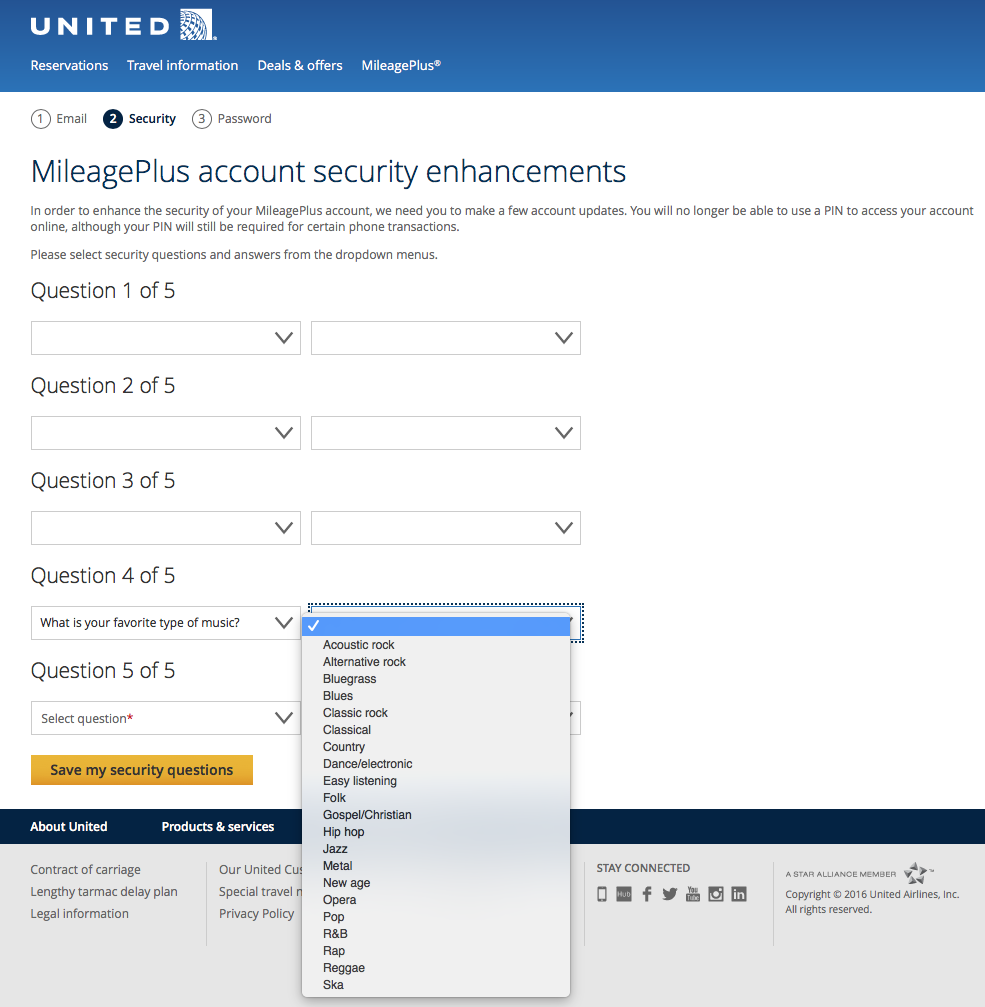
The latest twist on insecurity questions solves that problem for hackers, while making it harder for the account owner whose answers differ from the norm to remember the answers. Instead of a free-form input, you’re provided with a small number of valid answers. I discovered this the last time I went to log in to my United Airlines MileagePlus account. They required that I change my answers, and instead of being allowed to type my own answers, I was forced to choose an answer from a small list.
Now, if your theory is that insecurity questions are there to help the owners of accounts, it’s unlikely that you would have predicted this development. It’s insane, because it does little to help you, the account owner who has forgotten their password but does know your dog’s breed, and everything to help hackers. It’s even worse if your favorite genre or favorite dog is not listed as an option. You’re very unlikely to remember which option you chose in its place—or you’re going to assist hackers by always choosing an item at the top of the list.
I noticed immediately that some of the lists were ridiculously small. The list of musical genres includes only twenty-one items. Jim Fenton went through a bunch of the questions and discovered that some of the questions involve months, which means that the number of answers is a mere twelve. It’s not going to take much of a security breach for a hacker’s computer program to cycle through the choices and come up with the right combination.
If that security breach is like this one described on Stack Exchange that interchanges answers, it’s going to make the month answers ridiculously easy to hack, for example.
- June 14, 2013: Jim Rockford comes to identity theft
-
I’m not sure exactly why this reminds me of The Rockford Files•. Probably it’s the episode where Rockford discovers an insurance fraud scheme based on birth certificates not being linked to death certificates.
This trick involves finding your social security number by looking up people who died but were born in the same location and day as you were born:
Researchers Alessandro Acquisti and Ralph Grossy… accessed the Social Security Administration’s Death Master File, a publicly-available (at a price) record of Americans who have died, including their SSN, birth and death dates.
The third piece of information they needed was the date and location of birth of test subjects. They found these details readily available for purchase from information brokers, or even divulged for free by users of Facebook and other social networking sites.
Since 1988, babies have been automatically assigned Social Security numbers at the time of birth. So, suppose you were born September 21, 1989 at 10:11 a.m. in Springfield, Mass. If there was a Death Master File entry on someone born in the same location as you on the same date, given that the numbers are assigned sequentially, it would narrow down what number you were assigned to one very close to the deceased.
While the researchers couldn’t usually determine the exact numbers of their subjects, they were able to eliminate enough that a hacker would have only 9 or 99 or 999 possible combinations to try, a problem easily solved with a brute-force attack.
As the authors of the study say, “If one can successfully identify all nine digits of a SSN in fewer than 10, 100 or even 1,000 attempts, that Social Security number is no more secure than a three-digit PIN.” In fact, your high-school locker was probably more secure than your Social Security number.
This trick appears to work for people born between 1988 and 2011, as, before that, social security numbers had to be requested—they weren’t automatic at birth. The more the state makes things more convenient for the state, the more they make the same thing more convenient for criminals.
- August 7, 2012: Mat Honan should read Mimsy
-
In The last four digits of your social security number, I wrote:
There is a sense in which this entire discussion is irrelevant: because the last four numbers of your SSN are what businesses ask for, they are all that a criminal sometimes needs to use your cash or credit.
Or your private information. Since the last four digits of your SSN are used as a de facto password, they’re all hackers need to get access to your accounts. Increasingly, it’s the last four digits of your credit card that’s becoming your password, as Mat Honan discovered recently. Amazon didn’t treat the last four digits of the credit card as securely as they should have. Hey, why should they, it’s only the last four digits, right? It didn’t help that Amazon, like Apple, makes it far too easy for strangers to add things like credit cards and emails to your account. A hacker got his last four credit card digits, and then went to Apple to reset Honan’s iCloud password.
Insecurity questions need to be able to be turned off. The likelihood that they’ll be used for hacking attempts needs to be taken much more seriously. Otherwise, passwords are easily bypassed. And when the insecurity questions themselves can be bypassed for the even less secure billing address and last four of credit card or SSN, that’s insane. At that point there really is no purpose to passwords.
- April 28, 2012: Insecurity questions on phones and at banks
-
David Kushner at GQ has an article about a guy who easily hacks into celebrity phones to grab photos and other information.
“You find the right pieces,” he says, “and then it unlocks.” There were favorite colors to ascertain. Elementary-school names. Social Security numbers. Chaney became an expert. He found old school names on Classmates.com, friends on Facebook, and hometowns on free directories like Intelius. “If they’ve had their names removed, their parents are probably still on there,” he says.
Earlier in the article, the hacker asks “How hard could this be if it’s happening all the time?”
The answer is, not hard at all, and it’s the fault of the phone companies (and, in the case of famous email hacks, email companies like Yahoo) for making passwords pointless. Who needs to steal a password when you can reset the password using public knowledge?1
When we first started discussing using a password-reset process at the University, I managed to hold it off for about a year. When it finally became mandated by the higher-ups, I made it optional, and opt-in. These things are horribly insecure, as we’ve seen over the last couple of years from high-profile hacks—and as hackers such as Chris Chaney have recognized. I didn’t see a point in making everyone’s account hackable when only a few people actually use the password reset service. Eventually, as our department grew, I was no longer part of the accounts team and several years ago we made insecurity questions mandatory.
Unfortunately, we’re not alone. Even my bank started requiring them a few years ago. It just came up again a few days ago when Apple started requiring the use of insecurity questions, too.2 I first noticed it attempting to download the Los Angeles Festival of Books app to my iPad. I canceled, hoping that reducing the security of my account was an optional feature, and I just couldn’t see how to get past it on the limited iPad interface. But on my desktop the next day, just before leaving, there was clearly no way around it.
- January 18, 2010: Tumbling to SSN privacy
-
Being right isn’t always satisfying. In June 2006, I wrote:
Giving out the last four digits of your Social Security number makes your entire number a lot more vulnerable. Armed with a computer and an on-line authorization site that doesn’t care if an SSN is checked every day, they probably won’t have any problem finding the rest. Your only hope is that they won’t want to.
Hadley Leggett interviewed privacy researcher Alessandro Acquisti in a July 2009 article on Wired:
There’s only a few short steps between making a statistical prediction about a person’s SSN and verifying their actual number, Acquisti said. Through a process called “tumbling,” hackers can exploit instant online credit approval services—or even the Social Security Administration’s own verification database—to test multiple numbers until they find the right one.
And that was without having the last four digits. Social Security Numbers should never have been used as a combination username and password.
- Social Security number at Wikipedia
- “The SSN is frequently used by those involved in identity theft, since it is interconnected with so many other forms of identification, and because people asking for it treat it as an authenticator. It is generally required by financial institutions to set up bank accounts, credit cards, and obtain loans, partially because it is assumed that no one except the person to whom it was issued will have it. Ironically enough, Social Security cards used to have the caption ‘Not for identification’, indicating that the cards and their number are not intended to be a form of identification.”
- Social Security Number Allocations
- “The first three (3) digits of a person’s social security number are determined by the ZIP Code of the mailing address shown on the application for a social security number.”
- High Group List of SSNs
- “This list shows the SSN area and group numbers that are in the process of being issued as of the date at the top of this page.”
More security
- On education, the left is mired in the fifties
- Why don’t schools have locked doors? Because when it comes to education, especially K-12, the left, as in so many things, is mired in the distant industrialized assembly-line past.
- How does Apple’s supposed anti-conservative bias matter?
- If you think Apple has a bias against conservatives or Christians, you definitely don’t want Apple to build a tool its employees can use to help guess an iPhone’s password.
- Should Apple enable exes to access their ex-spouse’s iPad?
- Chris Matyszczyk wants Apple to just believe someone who says their spouse died, and give access to their iPad, then claims that this is how everything else, from house titles to bank accounts work. Unfortunately, he’s not far off there.
- Form validation with in_array in PHP
- When validating form input, you often will use an array of valid responses. Watch out if some of those valid responses are integers!
More social security numbers
- Jim Rockford comes to identity theft
- It’s easy enough to guess an SSN, if you know the SSN of someone born at the same location and the same time.
- Mat Honan should read Mimsy
- “Because the last four numbers of your SSN are what businesses ask for, they are all that a criminal sometimes needs to use your cash or credit.”
- Insecurity questions on phones and at banks
- How important are the last four digits of your social security number? That and a high school yearbook can get a hacker your bank account.
- Tumbling to SSN privacy
- Guessing social security numbers based on the statistical analysis I talked about in “The last four digits of your social security number” now has a name: “tumbling”.